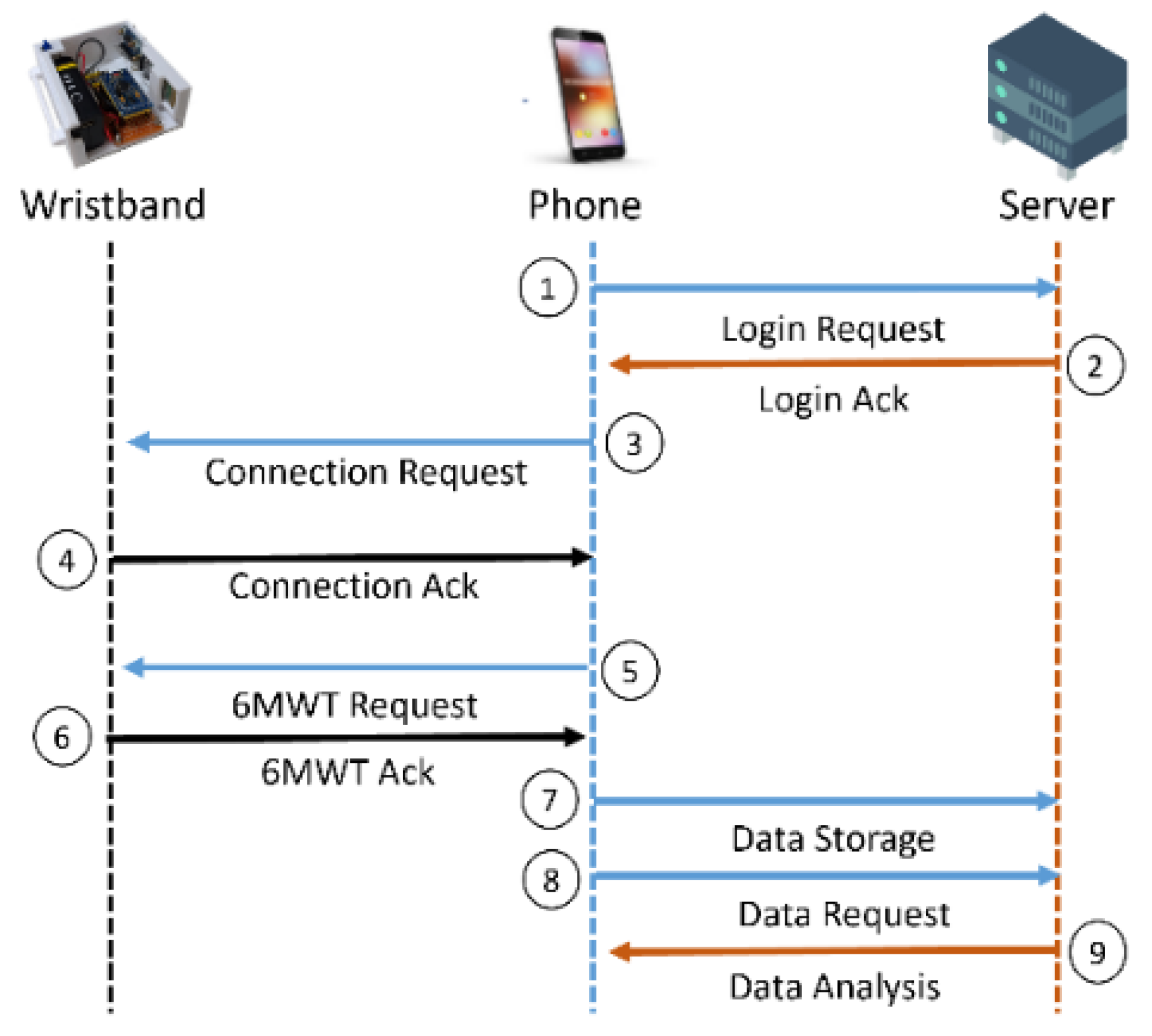
Biosensors | Free Full-Text | A Pervasive Pulmonary Function Estimation System with Six-Minute Walking Test
GitHub - sensepost/assless-chaps: Crack MSCHAPv2 challenge/responses quickly using a database of NT hashes
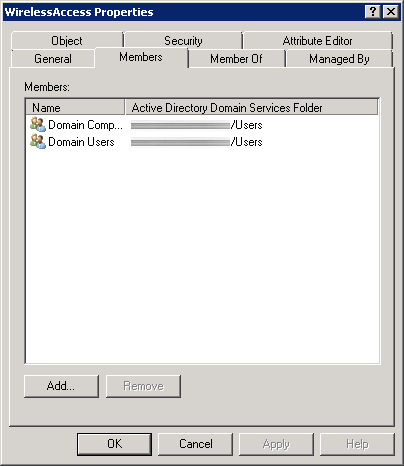
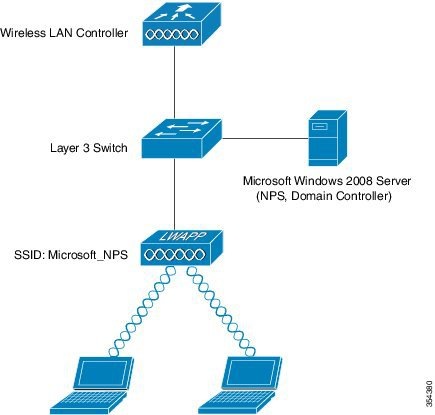
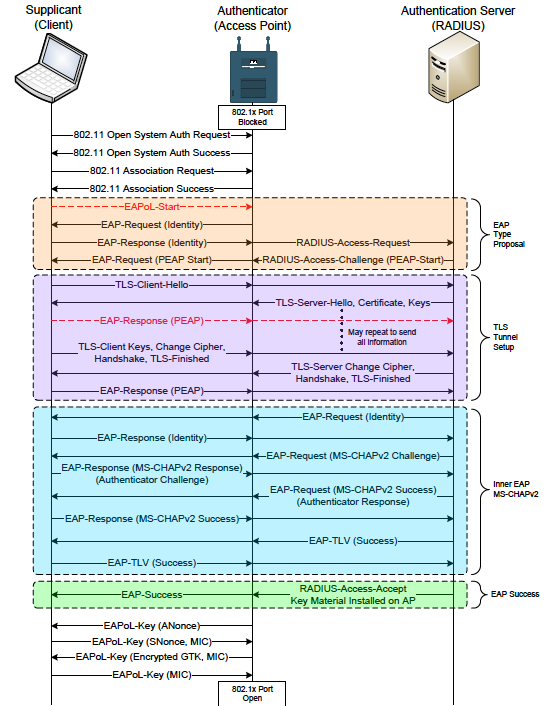
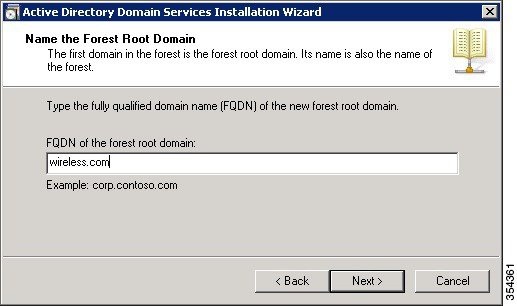
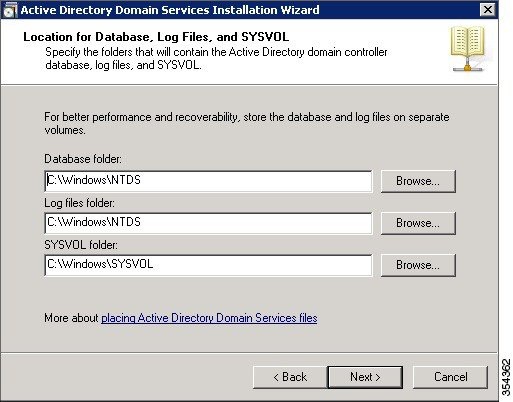
Tutorial: 802.1X Authentication via WiFi - Active Directory + Network Policy Server + Cisco WLAN + Group Policy - Jack Stromberg

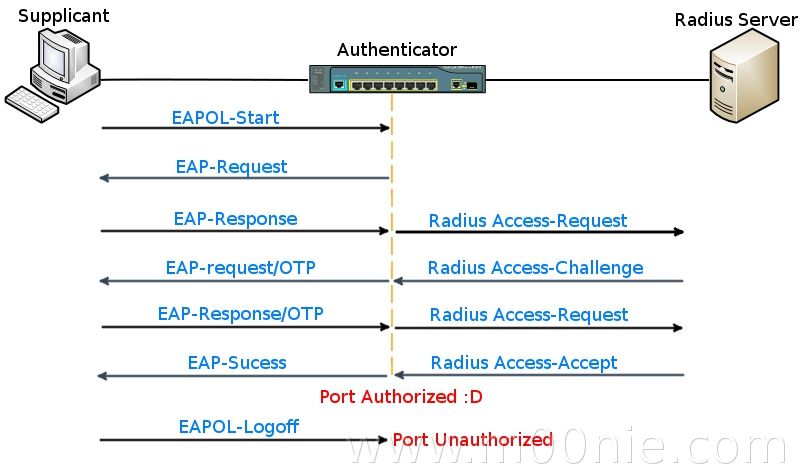
Addressing the WLAN Security Challenges > Cisco Unified Wireless LAN Security Fundamentals | Cisco Press
Short Paper: Exploiting WPA2-Enterprise Vendor Implementation Weaknesses through Challenge Response Oracles